When you picture a hacker, the first thing that pops into your head is a dark, hooded figure tapping away at a laptop, probably looking something like this. If you read the news, you'll have heard countless stories about data leaks and cyberattacks on commercial and government companies. Cybersecurity is rapidly emerging as an important issue in society as modern technology continues to evolve.
About a month ago (sorry, getting kind of lazy about writing) I participated in a hacking competition called picoCTF; however, it's not the kind of hacking that you think. Instead of encouraging its users to engage in suspicious or illegal activity, picoCTF provides a safe, legal platform for students to practice cybersecurity skills. Created by CMU, users participate in a series of online challenges and "reverse engineer, break, hack, decrypt, and think creatively and critically" in order to gain points on a live global leaderboard.
CTF stands for 'capture the flag', which means that in order to complete a challenge, users must locate a secret string of numbers and letters that might look something like this: picoCTF{3asY_P3a5y40407786}. Once entered into the online scoring system, you or your team will gain points. In this year's competition, challenges ranged from 100 points (easier) to 500 points (very complex).
This year was my first time ever trying my tech skills out on a CTF, and the experience was pretty cool. Here's a rundown of some of my favorite challenges from this year's competition.
'File types', 100 points
This file was found among some files marked confidential but my pdf reader cannot read it, maybe yours can. You can download the file from here.
Hint: Remember that some file types can contain and nest other files
Downloading the provided file seems to give you a mysterious pdf file that you can't open. If you place the file into the handy picoCTF browser-based webshell, you can investigate it using a Linux terminal.
Running the file command (file Flag.pdf), which will tell you any file type, I realized that the file was a Linux shell archive file. Opening it in a text editor revealed the special command needed to unzip the archive: sh Flag.pdf.
This yielded yet another mysterious file type. Using the file command showed that it was another type of strange archive. A quick google search showed what command I needed to use in order to unzip it.
In the end, the flag had originally been a plaintext file containing hexadecimal text, then zipped repeatedly about 10 times in exotic compression formats like LZOP and GZ.
Flag: picoCTF{f1len@m3_m@n1pul@t10n_f0r_0b2cur17y_79b01c26}
'Forbidden Paths', 200 points
Can you get the flag? Here's the website. We know that the website files live in /usr/share/nginx/html/ and the flag is at /flag.txt but the website is filtering absolute file paths. Can you get past the filter to read the flag?
The browser-based eReader appears to let you enter in a filename and display the contents of that file. Obviously, you can't type in "/flag.txt"; there is a 'Not Authorized' error because paths starting with / are absolute file paths.
Linux has a workaround, however: ".." stands for the parent directory, or the folder containing the current files. If you just type in ../../../ several times, you can go up folders as many times as you need to. The working directory is in /usr/share/nginx/html, so if you use the parent directory code four times, you can get to the root directory and access the flag. Try it out below:
Enter ../../../../flag.txt to get the flag.
Flag: picoCTF{7h3_p47h_70_5ucc355_6db46514}
'SideChannel', 400 points
This challenge presents you with a binary file that checks a PIN code:
There's something fishy about this PIN-code checker, can you figure out the PIN and get the flag?
Download the PIN checker program here pin_checker
Once you've figured out the PIN (and gotten the checker program to accept it), connect to the master server using nc saturn.picoctf.net 52680 and provide it the PIN to get your flag.
The program asks you for a PIN code, then tells you if it's correct or incorrect. Initially, I thought that the simplest way to crack the code was by brute-forcing it, but with 8 digits that would take months.
The hint says to read about 'timing-based side-channel attacks'. According to Wikipedia, this is a hacking method where the attacker uses the run time of a program to exploit and find out clues about what is inside.
For example, the following C++ code that checks whether two strings are equal is insecure:
bool insecureStringCompare(char *a, char *b, int length) {
for (int i = 0; i < length; i++) {
if (a[i] != b[i]) {
return false;
}
return true;
}
}
Since there is a loop that checks every character, and every iteration of the loop takes a very small time to run, you can theoretically measure the time taken to run this function in order to get clues about each character of the string.
To time the binary code in the challenge, I wrote a small Python program to automate the testing:
import time, os
while True:
input_code = int(input("What code do you want to test? "))
start = time.time()
os.system(f"echo {input_code} | ./pin_checker > /dev/null")
end = time.time()
print(f"Time taken to run: {end - start}")
The only thing left to do now is brute-force the password, but in a smarter way: one digit at a time, instead of every possible combination. For example: if '2' was the correct first digit in the password, then guessing '20000000' would run slower than '10000000' because the binary goes through another iteration of a loop.
After timing the numbers 00000000, 10000000, etc. up to 90000000, the test that took the longest and subsequently the first character in the password was obviously a 4. Repeating this with the next digit, I tested 40000000, 41000000, etc. up to 49000000 - and the test that took the longest was 48000000.
In the end, the correct password turned out to be 48390513 after testing all 8 digits. Connecting to the master server and entering the password yielded the flag.
Flag: picoCTF{t1m1ng_4tt4ck_9803bd25}
Final results
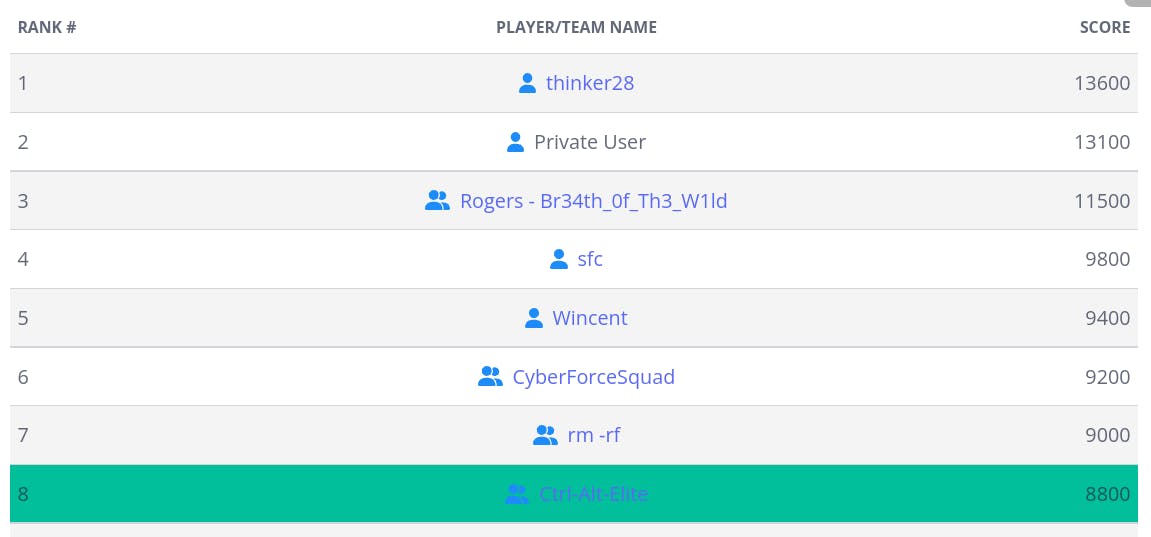
We did end up being defeated by some 7th graders (kudos to team rm -rf), but overall, I had a great competition experience and my team ended up 8th in the US out of middle schools. Plus I scored a free picoCTF T-shirt (don't ask, it's a long story).
I'll be looking forward to the next CTF competition. Until then, happy hacking.

